Let’s face it: you’ve meticulously crafted a cron job, scheduled it perfectly, and… nothing happens. Or worse,somethinghappens, but it’s not what you expected. One of the most common culprits behind mysteriously failing cron jobs is a permissions issue. This tutorial guides you through diagnosing and fixing cron permission problems, ensuring your scheduled tasks run reliably.
Understanding and correctly configuring cron permissions is crucial for maintaining system stability and preventing unintended consequences. A misconfigured cron job could lead to security vulnerabilities, data corruption, or service disruptions. By mastering cron permissions, you’ll gain the confidence to automate tasks safely and efficiently.
Here’s a quick tip to start with: Make sure the script you are trying to execute via cron is executable! Try running `chmod +x /path/to/your/script.sh`. This simple step resolves a surprising number of cron issues.
Key Takeaway: By the end of this tutorial, you'll be able to identify and resolve common cron permission problems, write secure and reliable cron jobs, and understand best practices for managing scheduled tasks on Linux systems.
Prerequisites
Before diving in, ensure you have the following: A Linux system: This tutorial is designed for Linux environments. While similar concepts apply to other Unix-like systems, the specific commands and paths might differ. I have tested this tutorial on Ubuntu 22.04. Basic Linux command-line skills: You should be comfortable using the terminal, navigating directories, and editing files. `cron` and `crontab` installed:Most Linux distributions come with cron pre-installed. If not, use your distribution's package manager (e.g., `apt install cron` on Debian/Ubuntu, `yum install cronie` on Cent OS/RHEL). Text editor: You'll need a text editor like `nano`, `vim`, or `emacs` to edit the crontab file. Root or `sudo` access: Some troubleshooting steps might require elevated privileges.
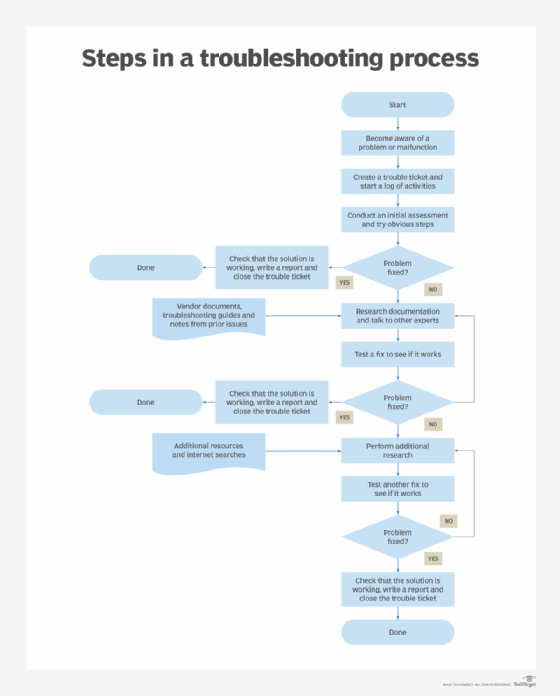
Overview of the Approach
The process of troubleshooting cron permissions involves a systematic approach:
1.Identify the user: Determine under which user account the cron job is intended to run. This is often the user who created the cron job, but it can also be specified explicitly in the crontab.
2.Check file permissions: Verify that the script being executed by cron has the correct permissions for the user running the cron job. This includes read, write, and execute permissions.
3.Check directory permissions: Ensure the user running the cron job has the necessary permissions to access the directory containing the script, as well as any directories the script interacts with.
4.Inspect the environment: Cron jobs run in a limited environment. Ensure that the script has access to the necessary environment variables and paths.
5.Review cron logs: Examine the cron logs for error messages that can provide clues about the cause of the permission problem.
6.Test interactively: Try running the script manually as the user who owns the cron job to replicate the environment and identify any issues.
7.Implement fixes: Adjust file permissions, modify the cron job, or update the script to resolve the permission problem.
This process helps narrow down the root cause and implement targeted solutions.
Step-by-Step Tutorial
Let's walk through two examples to illustrate how to troubleshoot and fix cron permission issues.
Example 1: Simple Script Execution
In this example, we'll create a simple script that writes the current date and time to a file. We'll then schedule this script to run every minute using cron and troubleshoot any permission issues that arise.
1. Create the Script
Create a script named `date_to_file.sh` in your home directory:
```bash
touch date_to_file.sh
chmod +x date_to_file.sh
nano date_to_file.sh
```
Add the following content to the script:
```bash
#!/bin/bash
Script to write the current date and time to a file.
DATE=$(date)
echo "$DATE" >> /tmp/date_output.txt
```
Explanation
`#!/bin/bash`: This shebang line specifies that the script should be executed using the bash interpreter. `DATE=$(date)`: This line captures the current date and time using the `date` command and stores it in the `DATE` variable. `echo "$DATE" >> /tmp/date_output.txt`: This line appends the value of the `DATE` variable to the `/tmp/date_output.txt` file.
2. Set Execute Permissions
Ensure the script is executable:
```bash
chmod +x date_to_file.sh
```
3. Create the Crontab Entry
Edit your crontab file:
```bash
crontab -e
```
Add the following line to schedule the script to run every minute:
```text /home/your_username/date_to_file.sh
```
Replace `your_username` with your actual username.
Explanation
``:This cron schedule means "run every minute." `/home/your_username/date_to_file.sh`: This is the absolute path to the script that cron will execute.
4. Verify Cron Installation
Verify that cron is running (most systems start it by default):
```bash
sudo systemctl status cron
```
5. Troubleshooting Permissions (if needed)
If the script doesn't run as expected, check the cron logs:
```bash
sudo grep CRON /var/log/syslog
```
Or, depending on your system:
```bash
sudo journalctl -u cron
```
If you see errors like "permission denied" or "cannot open file," it indicates a permission issue.
Problem: The script might not have execute permissions, or the user running the cron job might not have permission to write to the `/tmp/date_output.txt` file. Solution:
Ensure the script has execute permissions: `chmod +x date_to_file.sh`
Verify the user running the cron job (usually the user who created the crontab) has write access to `/tmp/`. A more robust solution is to write to a user-owned directory (e.g., `$HOME/date_output.txt`).
If necessary, change the owner of the `/tmp/date_output.txt` file: `sudo chown your_username:your_username /tmp/date_output.txt`
6. Test After Fixing
After applying the fix, wait a minute and check the `/tmp/date_output.txt` file:
```bash
cat /tmp/date_output.txt
```
You should see the date and time appended to the file every minute.
Example 2: Advanced Script with Locking and Environment Variables
This example demonstrates a more robust script that includes locking to prevent overlapping executions and uses environment variables for configuration.
1. Create the Script
Create a script named `backup_script.sh`:
```bash
touch backup_script.sh
chmod +x backup_script.sh
nano backup_script.sh
```
Add the following content to the script:
```bash
#!/bin/bash
Backup script with locking and environment variables.
Requires:
BACKUP_SOURCE_DIR: Directory to back up.
BACKUP_DESTINATION_DIR: Directory to store the backup.
Set -e to exit immediately if a command exits with a non-zero status.
set -e
Define lock file location
LOCK_FILE="/tmp/backup_script.lock"
Function to acquire a lock
acquire_lock() {
if [ -e "$LOCK_FILE" ]; then
echo "Another instance is already running. Exiting."
exit 1
fi
touch "$LOCK_FILE"
}
Function to release the lock
release_lock() {
rm -f "$LOCK_FILE"
}
Acquire the lock
acquire_lock
Check if environment variables are set
if [ -z "$BACKUP_SOURCE_DIR" ]
| [ -z "$BACKUP_DESTINATION_DIR" ]; then |
|---|
| echo "Error: BACKUP_SOURCE_DIR and BACKUP_DESTINATION_DIR must be set." |
| release_lock |
| exit 1 |
| fi |
Perform the backup
tar -czvf "$BACKUP_DESTINATION_DIR/backup_$(date +%Y%m%d%H%M%S).tar.gz" "$BACKUP_SOURCE_DIR"
echo "Backup completed successfully."
Release the lock
release_lock
```
Explanation
`#!/bin/bash`: Specifies the bash interpreter. `set -e`: Exits the script immediately if any command fails. Essential for robust scripting. `LOCK_FILE="/tmp/backup_script.lock"`: Defines the path to the lock file, used to prevent concurrent executions. `acquire_lock()` and `release_lock()`: Functions to create and remove the lock file.
Environment variable checks: The script checks if `BACKUP_SOURCE_DIR` and `BACKUP_DESTINATION_DIR` are set. `tar -czvf ...`: Creates a compressed tar archive of the source directory.
Error handling: The script exits gracefully if environment variables are missing or if another instance is running.
2. Set Environment Variables
Instead of hardcoding paths, let's use environment variables. Important:Donotstore secrets directly in the script. Use environment variables or, better yet, a dedicated secrets manager.
Create a file named `.env` in your home directory (or a more secure location with restricted permissions):
```bash
nano .env
```
Add the following lines, replacing the paths with your desired values:
```text
BACKUP_SOURCE_DIR=/home/your_username/source_data
BACKUP_DESTINATION_DIR=/home/your_username/backup_data
```
Replace `your_username` with your actual username. Also, create the `source_data` and `backup_data` directories:
```bash
mkdir ~/source_data
mkdir ~/backup_data
Create a dummy file to test
touch ~/source_data/dummy_file.txt
```
Source the environment variables before running the script. While sourcing directly in the crontabcanwork, it's generally better to handle it within the script or via a wrapper. For testing, do this:
```bash
source .env
```
3. Create the Crontab Entry
Edit your crontab:
```bash
crontab -e
```
Add the following line:
```text source /home/your_username/.env && /home/your_username/backup_script.sh
```
Replace `your_username` with your actual username.
Explanation
`source /home/your_username/.env`: Loads the environment variables from the `.env` file. `&&`: Ensures the backup script is executed only if sourcing the `.env` file is successful.
4. Troubleshooting
If the script fails, check the cron logs:
```bash
sudo grep CRON /var/log/syslog
```
Common issues: Environment variables not set: The script might fail if the `BACKUP_SOURCE_DIR` or `BACKUP_DESTINATION_DIR` environment variables are not set within the cron environment. Sourcing the `.env` file in the crontab entry resolves this. Lock file conflict: If the script is still running from a previous execution, the lock file will prevent the new execution from starting. Check if the lock file exists (`/tmp/backup_script.lock`) and, if so, investigate why the previous execution didn't complete. Permissions on source/destination directories: Ensure the user running the cron job has read access to `BACKUP_SOURCE_DIR` and write access to `BACKUP_DESTINATION_DIR`. Permissions on .env file: Ensure only the owner can read the .env file (chmod 600 .env).
5. Testing After Fixing
After fixing any issues, wait a minute and check the `backup_data` directory:
```bash
ls -l ~/backup_data
```
You should see a new backup archive created every minute.
Use-case Scenario
Cron jobs are commonly used to automate database backups. For example, a nightly cron job can execute a script that dumps a database, compresses the dump, and stores it in a secure location. Properly configured permissions ensure that the backup script can access the database credentials and write the backup file to the designated directory without compromising security.
Real-world mini-story
A Dev Ops engineer named Sarah was struggling with intermittent failures in her team's nightly database backups. After digging through cron logs, she discovered that the backup script was sometimes failing with "permission denied" errors. She realized that the user running the cron job didn't have consistent write access to the backup directory. By adjusting the directory permissions and ensuring the cron job ran under a dedicated service account, she eliminated the permission issues and ensured reliable database backups.
Best practices & security
File permissions: Ensure scripts are owned by the appropriate user and group, and have the minimum necessary permissions (e.g., `chmod 755 script.sh`). Avoiding plaintext secrets: Never store passwords or sensitive information directly in scripts. Use environment variables, encrypted configuration files, or a dedicated secrets manager. Ensure the configuration file is readable only by the owner. Limiting user privileges: Run cron jobs under dedicated user accounts with limited privileges. This minimizes the impact if a cron job is compromised. Log retention: Implement a log rotation policy to prevent cron logs from filling up disk space. Timezone handling:Be mindful of timezones. Explicitly set the `TZ` environment variable in the crontab or use UTC for server time.
Troubleshooting & Common Errors
"Permission denied" errors: This usually indicates that the script doesn't have execute permissions or the user running the cron job doesn't have the necessary read/write permissions.
Fix: Use `chmod +x script.sh` to make the script executable. Check directory permissions with `ls -l` and adjust with `chown` and `chmod` as needed. "Command not found" errors: This can happen if the script relies on commands that are not in the cron environment's `PATH`.
Fix: Use absolute paths to all commands in the script or explicitly set the `PATH` environment variable in the crontab. Cron job not running: If a cron job doesn't run at all, check the cron logs for errors. Also, verify that the cron service is running (`sudo systemctl status cron`). Check the crontab file for syntax errors. Testing:Use `run-parts --test /etc/cron.hourly` (or daily/weekly/monthly) to check which scripts would be run (without actually running them).
Monitoring & Validation
Check job runs: Regularly check the cron logs (`/var/log/syslog` or `journalctl -u cron`) for errors or unexpected behavior. Exit codes: Pay attention to the exit codes of cron jobs. A non-zero exit code indicates an error. You can add error handling to your scripts to log exit codes and send alerts. Logging: Implement robust logging within your scripts to track their execution and identify potential problems. Alerting patterns: Set up alerts to notify you of cron job failures or unusual activity. This can be done using tools like `Monit`, `Nagios`, or cloud-based monitoring services.
Alternatives & scaling
Cron vs. systemd timers: For more complex scheduling requirements or tighter integration with system services, consider using systemd timers instead of cron. Systemd timers offer more flexibility and control. Kubernetes cronjobs: In containerized environments, Kubernetes cronjobs provide a robust and scalable way to schedule tasks. CI schedulers:CI/CD systems like Jenkins or Git Lab CI can be used to schedule tasks, especially those related to software builds, testing, and deployment.
FAQ
What user does cron run jobs as?
By default, cron jobs run as the user who owns the crontab. System-wide cron jobs (defined in `/etc/crontab`) can specify a different user using the `run-as` field.
How can I see the output of my cron job?
Redirect the output of your cron job to a file or use the `mail` command to send the output to your email address. For example: `/path/to/script.sh > /tmp/cron_output.log 2>&1` redirects both standard output and standard error to `/tmp/cron_output.log`.
Why isn't my cron job running even though the crontab is correct?
Common reasons include: incorrect file permissions, errors in the script, the cron service not running, or the script relying on environment variables that are not set in the cron environment. Check the cron logs for error messages.
Can I use wildcards in cron job paths?
No, cron doesn't support wildcards in the path to the script. You must specify the absolute path to the script.
How do I schedule a cron job to run at system startup?
Cron is not the ideal tool for running tasks at system startup. Use systemd services instead, as they are designed for this purpose.
Conclusion
Troubleshooting cron permissions can be frustrating, but with a systematic approach and a solid understanding of file permissions, environment variables, and cron logs, you can conquer even the most stubborn scheduling issues. Always test your cron jobs thoroughly after making changes to ensure they run reliably and securely.
